Tampilkan postingan dengan label post-exploitation. Tampilkan semua postingan
Tampilkan postingan dengan label post-exploitation. Tampilkan semua postingan
- Home
- post-exploitation
post-exploitation
Backdoor using Netcat, cryptcat , ncat.
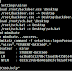
Today we are gonna talk about Netcat & its alternative ; i assume that all of you are familiar with Netcat. If not than read here . Als...
Get shell using Missing Autoruns.
In previous post we saw that how can we execute schedule task after compromised PC.Today we will see another method to maintaining access o...
Schedule Task in windows after Exploitation.
Recently in Derbycon mubix & carnal0wnage present "windows attacks at is the new black ". It`s really great presentation . Y...
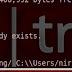
Extract & decrypt Chrome & IE passwords from Remote PC
In previous post i mentioned how we can extract saved passwords from firefox & thunderbird from rempote PC. Today we are going to extra...
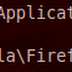
Extract & decrypt passwords from Firefox & Thunderbird.
Today we are going to extract password from Fireox & Thunderbird which are saved in browser and then try to decrypt that passwords from ...
Post exploitation & swaparoo backdoor.
Today we are going to create valid RDP user in victim pc using two method. (1)As usual get meterpreter session of victim using metasploit.We...
Post exploitation using Nishang.
Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security and post exploitation...
Langganan:
Postingan (Atom)